OAuth 2.0 in Depth.mp4
This presentation talks about Why OAuth 2.0 came into picture, What it is, How to use it Shows practical example of OAuth 2.0 on Facebook and Google It also talks about OpenID History, how it is different than OAuth. The next steps in OpenID that is OpenID Connect (in theory)
Table of Contents:
00:06 - OAuth 2.0 in Depth
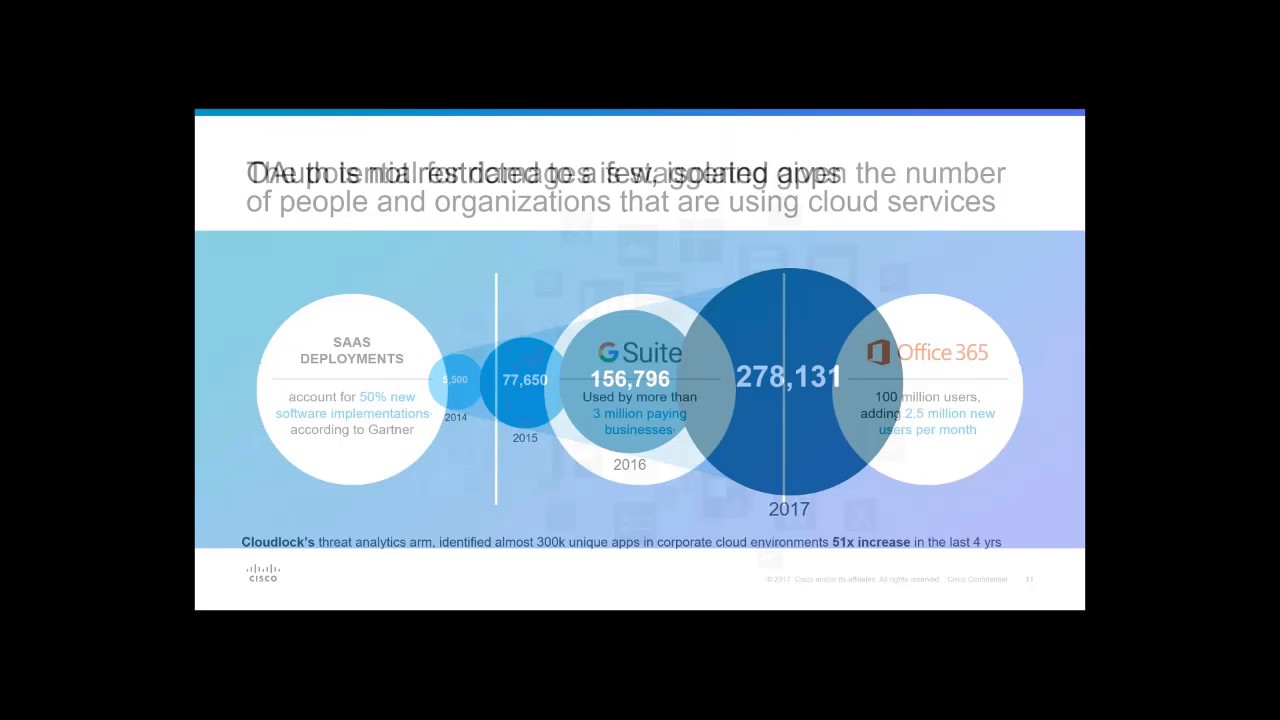
00:14 - Why study about OAuth?
01:11 -
01:43 -
05:16 -
05:55 -
06:14 - Security
06:54 - OAuth In a Nut Shell
07:36 - OAuth In a Nut Shell
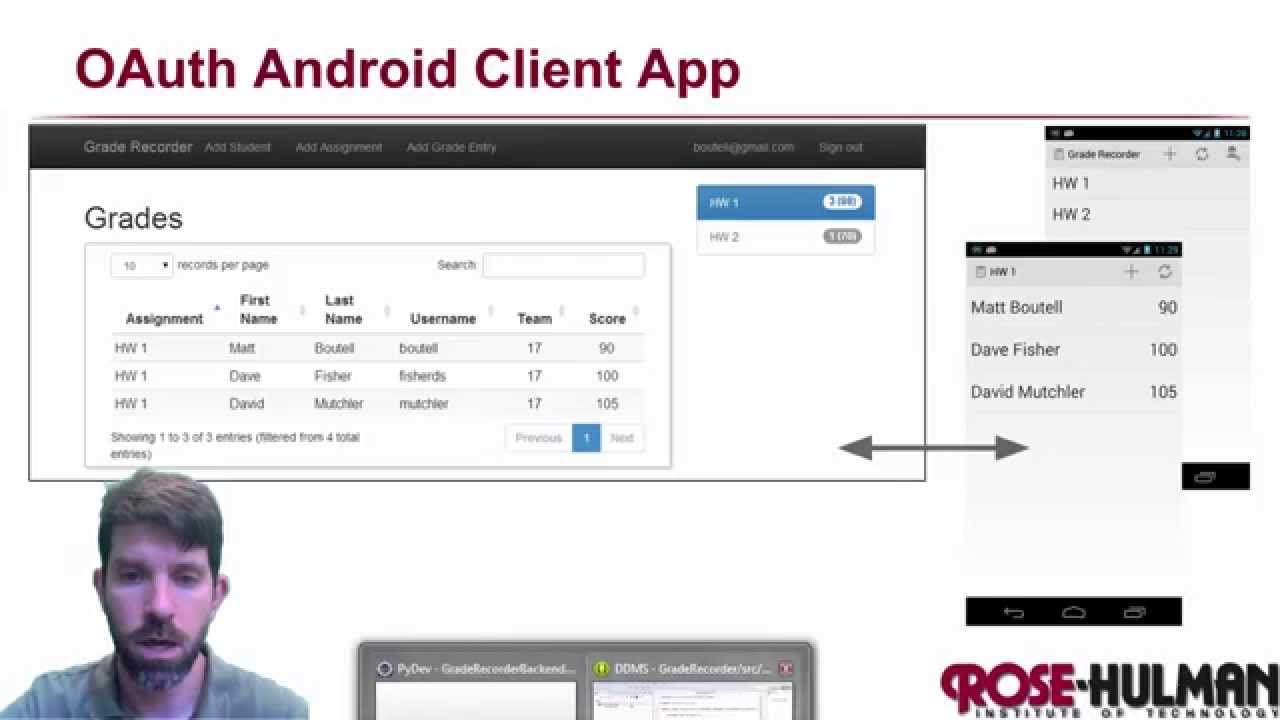
08:48 - OAuth Practical Example
08:55 - Without OAuth
09:09 - Without OAuth
09:26 - Without OAuth
09:30 - Lets Start Again
09:34 - With OAuth
09:45 - With OAuth
09:59 - With OAuth
10:32 - With OAuth
17:30 - Lets get Technical
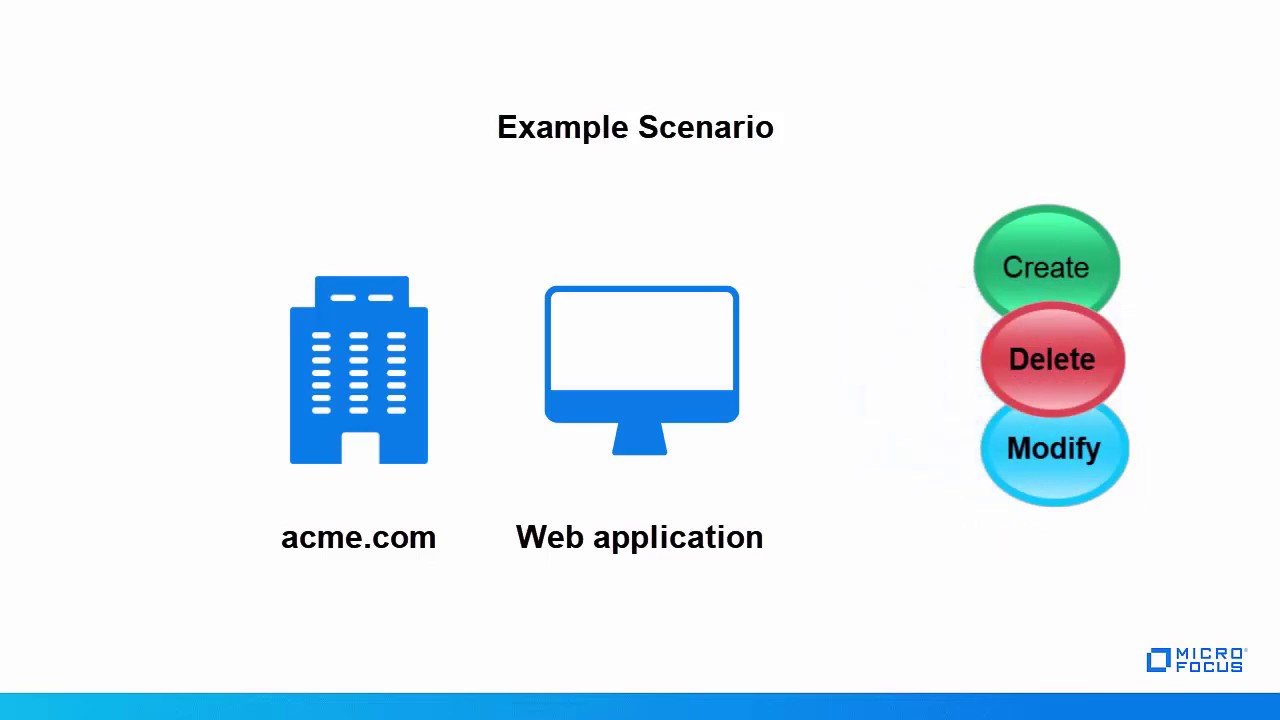
17:32 - Why OAuth is required?
19:51 - Why OAuth is required?
20:14 - Why OAuth is required?
21:39 - Why OAuth is required?
21:40 - Understand OAuth Roles
21:44 - Roles
22:25 - Resource Owner
22:27 - Resource Server
22:29 - Client
22:29 - Authorization Server
22:30 -
26:08 - Pre Requisite for OAuth
26:32 -
26:47 -
27:37 -
27:41 -
27:48 -
27:57 - Pre Requisite for OAuth
30:19 - Tools used to try OAuth
31:42 - Tools used to try OAuth
31:42 - Different ways to Do OAuth
31:48 - Grant Types
32:18 -
34:19 -
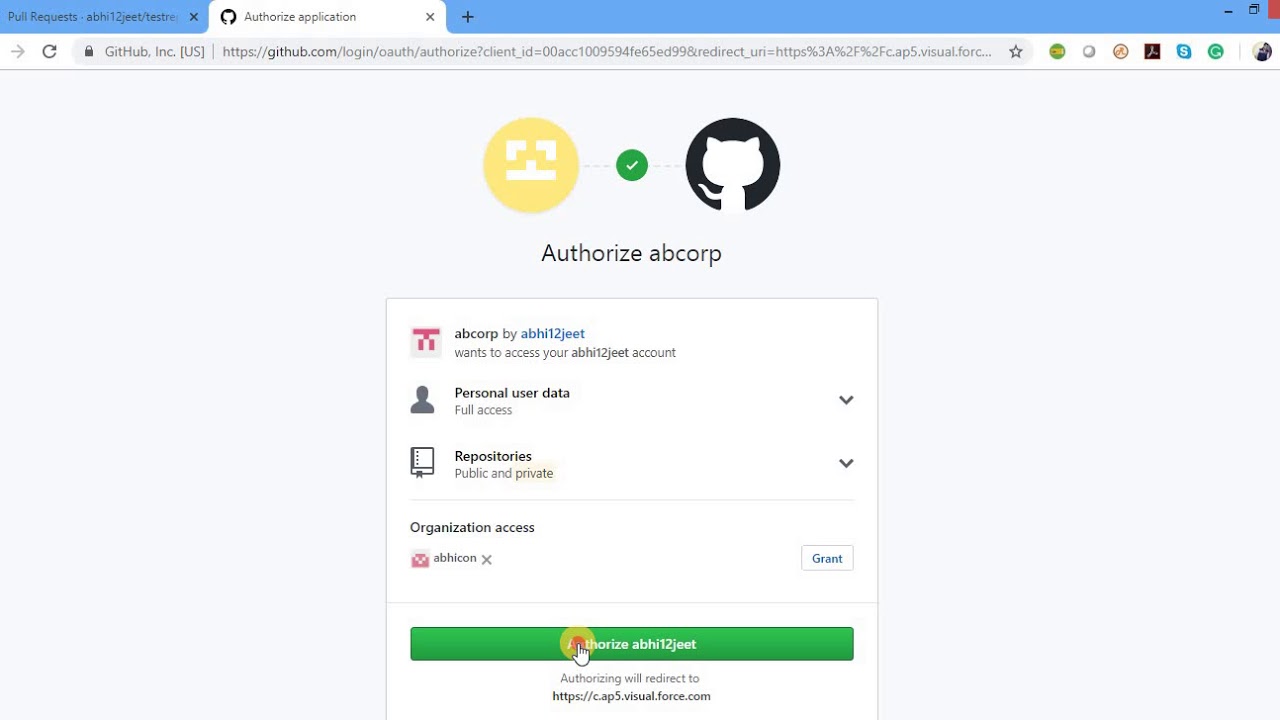
35:07 - Live Example Facebook
39:36 - Live Example Facebook
39:37 - Step 1 -- Get Authorization Code
39:37 - Understanding the URL
39:39 -
55:00 -
55:01 -
55:01 -
55:02 -
55:03 -
59:03 -
59:03 - Live Example Facebook
59:04 - Step 1 -- Get Authorization Code
59:04 - Understanding the URL
59:05 -
59:06 - Understanding the URL
59:06 - Step 1 -- Get Authorization Code
59:06 - Live Example Facebook
59:07 -
59:17 - Live Example Facebook
59:17 - Step 1 -- Get Authorization Code
59:18 - Understanding the URL
59:18 -
59:19 -
59:19 -
59:19 - Step 2 -- Exchange to get Access Code
59:20 - Important Note
59:21 - Understanding the URL
59:21 - Step 3 -- Access Protected Resource
59:22 - Facebook Protected Resource
59:22 - Facebook Protected Resource
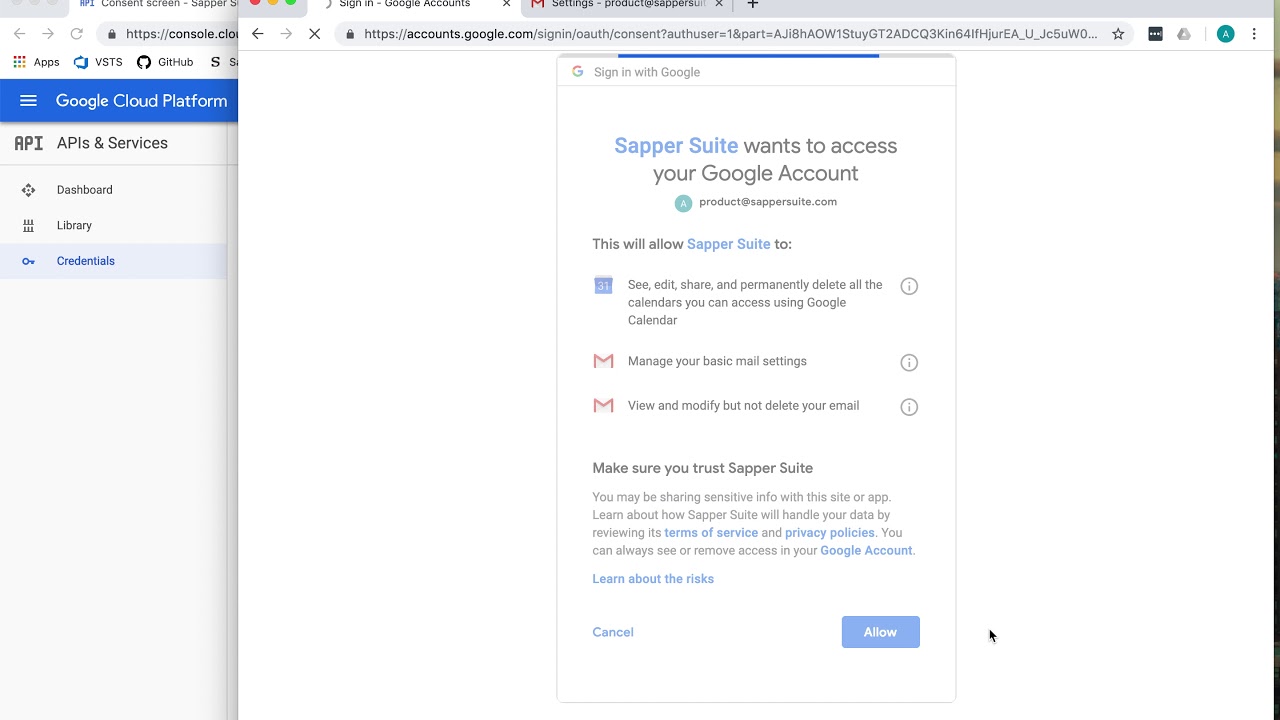
59:23 - Live Example Google
59:23 - Step 1 -- Get Authorization Code
59:23 - Understanding the URL
59:24 -
59:24 -
59:24 -
59:25 -
59:25 - Step 2 -- Exchange to get Access Code
59:26 - Step 3 -- Access Protected Resource
59:26 - Google Protected Resource
59:27 - What happens when access token expires?
59:28 - Use Refresh_Token to Issue Access_Token
59:28 - Grant Types
59:39 -
01:02:33 -
01:02:33 - Live Example Facebook
01:03:17 - Grant Types
01:03:51 -
01:05:56 - Use Cases
01:05:59 - Grant Types
01:09:38 -
01:09:51 - Use case
01:09:52 - Use case
01:09:54 - OAuth from Mobile Device
01:10:12 - Popular Approaches
01:10:49 -
01:11:47 - Disclaimer
01:12:01 - Request Authorization
01:13:06 - Authenticate and Approve
01:13:14 - Approve
01:13:29 - Handle Callback
01:15:06 - Handle Callback
01:15:07 -
01:15:42 -
01:15:58 - Trade Code for Token(s)
01:16:05 - Using an Access Token
01:17:08 - Pros and Cons
01:17:43 - Popular Approaches
01:17:52 -
01:19:10 - Pros and Cons
01:27:08 - Open ID Story
01:27:31 - Example of OpenID
01:30:05 - What are you doing?
01:30:18 - Another Example
01:30:57 - Wait!!
01:30:59 -
01:33:18 -
01:33:19 - Behind the Scene
01:33:43 - Behind the Scene
01:34:27 - Difference between OpenID and OAuth
01:34:52 - Next Steps : OpenID Connect
01:35:06 - Disclaimer
01:35:16 - OpenID Connect
01:36:18 - OpenID Connect
01:36:18 - OpenID Connect
01:36:45 - Let's see a Dummy Flow
01:36:46 - Step 1 -- Get Access_Code and ID_Token
01:37:12 - Build the OAuth URL for id_token & access_token (implicit grant flow)
01:38:43 - Build the OAuth URL for id_token & access_token (implicit grant flow)
01:38:45 - Dummy Response
01:39:38 - ID_Token
01:39:39 - Step 2 -- Verify the Identity by going to Check ID End Point
01:39:49 - Verify with Check ID End Point
01:40:22 - What does the response mean?
01:41:08 - Step 3 -- Get User Info from UserInfo EndPoint
01:41:29 - UserInfo EndPoint is a special resource accessed by providing access_token
01:43:07 - Reference
-
Category












No comments found